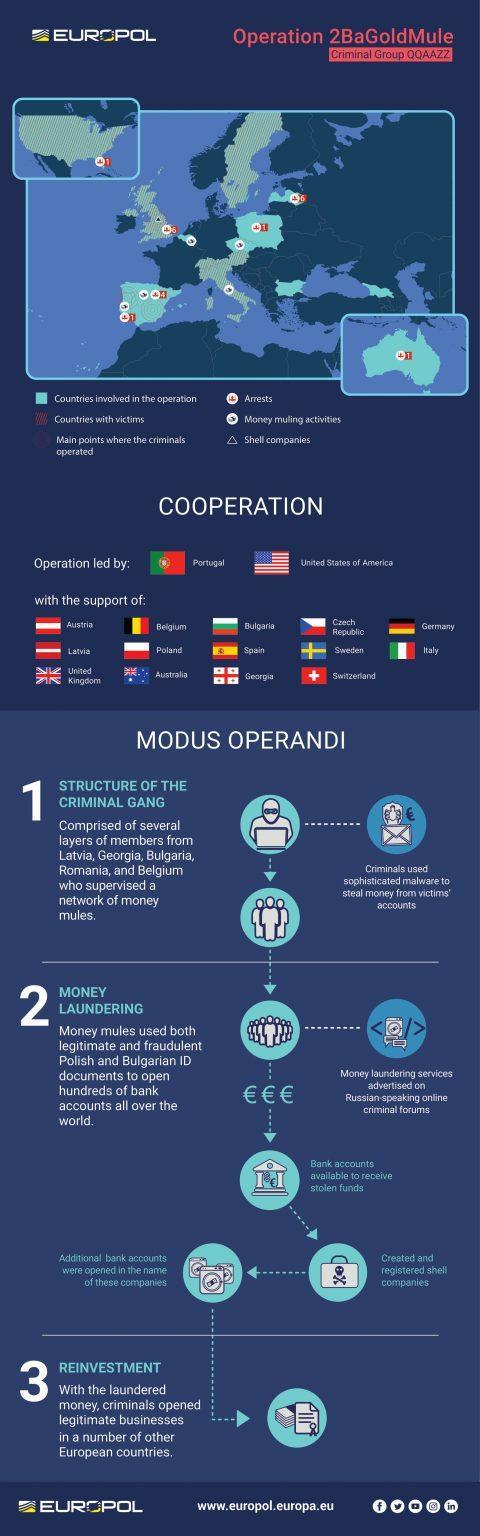
Law enforcement authorities from 16 different countries have disrupted the QQAAZZ money laundering network, carrying out 40 house searches and arresting 20 suspected members of the group.
In an international operation described by Europol as “unprecedented”, houses were searched in Latvia, Bulgaria, the United Kingdom, Spain and Italy. The largest number of searches in the case were carried out in Latvia, while Bitcoin mining equipment was seized in Bulgaria.
It is estimated that the QQAAZZ network laundered, or attempted to launder, tens of million Euros of stolen funds since 2016.
According to Europol, QQAAZZ was comprised of members mainly from Latvia, Georgia, Bulgaria, Romania, and Belgium. It opened and maintained hundreds of corporate and personal bank accounts at financial institutions throughout the world to receive money from cybercriminals who stole it from accounts of victims.
The funds were then transferred to other QQAAZZ-controlled bank accounts and sometimes converted to cryptocurrency using ‘tumbling’ services designed to hide the original source of the funds. After taking a fee of up to 50-percent, QQAAZZ returned the balance of the stolen funds to their cybercriminal clientele.
The QQAAZZ members secured these bank accounts by using both legitimate and fraudulent Polish and Bulgarian identification documents to create and register dozens of shell companies which conducted no legitimate business activity. Using these registration documents, the QQAAZZ members then opened corporate bank accounts in the names of the shell companies at numerous financial institutions within each country, thereby generating hundreds of QQAAZZ-controlled bank accounts available to receive stolen funds from cyber thieves.
QQAAZZ advertised its services as a “global, complicit bank drops service” on Russian-speaking online cybercriminal forums where cybercriminals gather to offer or seek specialised skills or services needed to engage in a variety of cybercriminal activities.
A Europol spokesperson said the criminal gangs behind some of the world’s most harmful malware families, such as Dridex, Trickbot and Goznym, feature among those having benefited from the services provided by QQAAZZ.
The house searches and arrest follow a complex investigation led by the Portuguese Judicial Police together with the United States Attorney Office for the Western District of Pennsylvania and the FBI’s Pittsburgh Field Office, alongside the Spanish National Police and the regional Catalan police and law enforcement authorities from the United Kingdom, Latvia, Bulgaria, Georgia, Italy, Germany, Switzerland, Poland, Czech Republic, Australia, Sweden, Austria and Belgium with coordination efforts led by Europol.
Edvardas Šileris, Head of European Cybercrime Centre, Europol said: “Cybercriminals are constantly exploring new possibilities to abuse technology and financial frameworks to victimise millions of users in a moment from anywhere in the world.
“Today’s operation shows how through a proper law enforcement international coordination we can turn the table on these criminals and bring them to justice.”
How the QQAAZZ network operated:
























No comments yet